Security
DataZen implements security at multiple levels including DataZen Manager, DataSync Agents, and Change Logs.
This section provides an overview of various security features available.
DataZen Manager
DataZen Manager does not store sensitive data directly. However, it provides management screens that display and send sensitive data to DataSync Agents. As a result, DataZen Manager offers a few security options to help keep sensitive data secure.
DataZen Manager communicates to an agent using the API exposed by the agent through the HTTP protocol. By default, an agent is configured to listen on port 9559. To secure this communication you can bind an SSL certificate to port 9559, or change the port to 443. Even without SSL encryption, connection strings are transferred encrypted by DataZen. See the Connection Strings section below for more information.
Authentication & Authorization
DataZen Manager requires users to be authenticated on the local machine and as such implements a single sign-on
mechanism with the local Windows operating system. However, DataZen Manager does not by itself provide any information
or configuration settings that is sensitive in nature, so no additional authentication or authorization is
implemented by DataZen Manager, until you register an agent. Accessing a DataSync Agent requires authentication and authorization.
Security Group Access Control
To configure access to a DataSync Agent, after it has been registered, choose Configuration->Agent Settings.
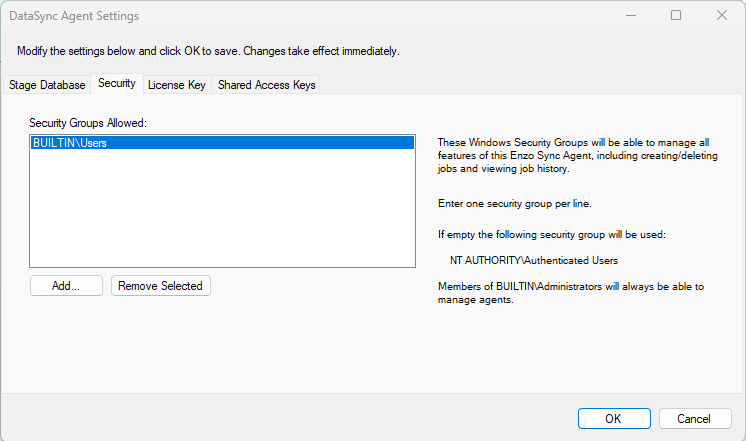
Members of the BUILTIN\Administrators group can always access a DataSync Agent on Windows where both the agent and the manager are running. However, remote administration requires additional configuration.
You can use this screen to add additional security groups. All users in the security groups listed in this screen will be able to fully manage and administer the selected DataSync Agent.
Shared Access Keys
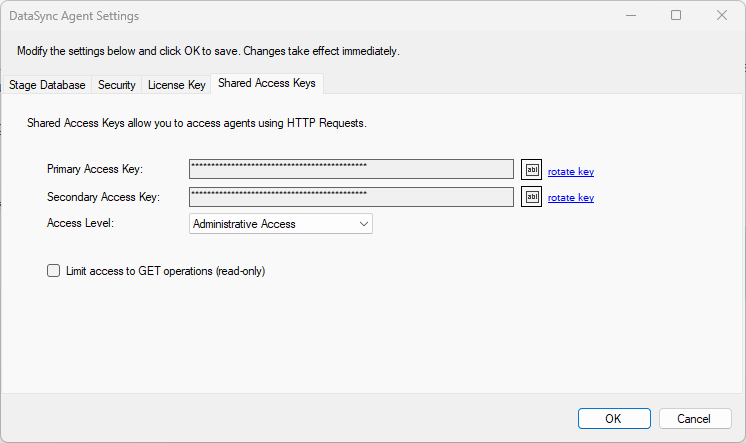
By default, Shared Keys are disabled. However, when enabled, you can choose the level of access to the DataSync Agent: Administrative, Agent API, Jobs API. You can also limit access to these APIs to GET operations only (read-only).
These keys can be used to connect to a DataSync Agent using DataZen Manager or through programmatic means, including Postman and Fiddler. See the DataSync Agent API documentation for more information.
Connection Strings
Most screens showing connection strings do not actually load secrets on the screen; instead, most screens display the Connection Key of the selected connection string. However, the Connection String management screens do display and save full connection string secrets. Anytime a connection string secret is read, or saved, the connection string is encrypted. This ensures that even if no SSL encryption is enabled on the DataSync Agent HTTP port connection secrets are encrypted on the wire.
Connection strings are encrypted using AES and are stored with a Vector (Salt). They can be accessed using the GET Connections operation if the Shared Access Keys are enabled for the Agent API.
DataSync Agent
SSL Encryption
Unless specifically configured to listen on a different port, agents listen on HTTP port 9559 on an unencrypted HTTP channel. To secure administrative traffic to your agent, you can install an SSL certificate and bind it to the listening port to enable HTTPS communication.
To bind EnzoDS.exe to port 443 on your local server, change the
appSettings section of the
settings file (EnzoDS.exe.Config) as
follows:
<add key="listenerPort" value="443" /> <add key="listenerUrl" value="https://SERVERNAME" />
This section provides high level information on how to create and configure a self-signed SSL certificate
on port 443, for a test environment. For production environments, it is recommended to use a public
Certificate Authority to obtain a certificate for your server instead.
-
Create a CA Certificate
makecert -n "CN=datazen" -r -sv datazen.pvk datazen.cer
Once created, add this certificate to your Trusted Root Certification Auhorities store.
-
Create an SSL Certificate
Replace YOURSERVERNAME below with you actual server name.makecert -sk DataZenSSL -iv datazen.pvk -n "CN=YOURSERVERNAME" -ic datazen.cer datazenssl2.cer -sr localmachine -ss My
This command will generate an SSL certificate and add it to the My certificate store.
-
Find the SSL Cert Thumbprint (MMC Snap-In)
Using MMC (Certificate Snap-In) find the SSL certificate you just created in the Personal\Certificate store (My) and copy its Thumbprint in memory.
-
Bind SSL to Port 443 (IPv4 and IPv6)
Replace the certhash value with Thumbprint abovenetsh http add sslcert ipport=0.0.0.0:443 certhash=THUMBPRINT appid={0abc7514-3558-4142-b81b-79149673bf57} certstorename=MY usagecheck=disable netsh http add sslcert ipport=[::]:443 certhash=THUMBPRINT appid={0abc7514-3558-4142-b81b-79149673bf57} certstorename=MY usagecheck=disable
Auditing
DataZen stores a detailed log of actions taken on its API in the database.
A summary of jobs that have been executed is stored in the jobexecutions table, while the
details of each execution are stored in the executionauditlog table.
In addition, it is possible to log all activities to disk. Enabling this feature is only recommended
during testing for performance reasons. To enable the disk audit log, add an entry in the
appSettings section of the EnzoDS.exe.Config file:
<add key="logFile" value="c:\tmp\enzodslog.txt" />

